This post is a tutorial on how to use IceBuddha and it's parse scripts in performing some malware analysis on Mini Duke.
On February 27, 2013, Kaspersky Labs released a paper The MiniDuke Mystery: PDF 0-day Government Spy Assembler 0x29A Micro Backdoor. The paper states that the Mini Duke PDF exploit connects to artas[dot]org/engine/index.php (and some other domains) where it downloads a gif file that contains an encrypted backdoor.
I grabbed a copy of one of the files (bg_afvd.gif: md5sum 92a2c993b7a1849f11e8a95defacd2f7). I put the file in a password protected zip, using the same password scheme as http://contagiodump.blogspot.com, and you can download it here: bg_afvd.gif.zip (md5sum: 39664ffaf93d8961d1498de8a7c49807). It's just a normal .gif file with some data appended to the end, so it can't infect you, but it's always good to take precautions.
IceBuddha has the ability to parse .gif files. You can take a look at one by going to http://icebuddha.com/index.htm?test=sample_1.gif
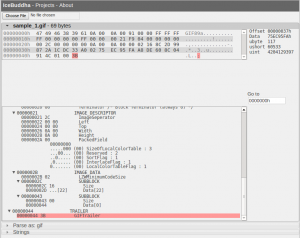
This sample file is the same one used by http://www.matthewflickinger.com/lab/whatsinagif/bits_and_bytes.asp which is an excellent explanation of the GIF file format.
When I look at bg_afvd.gif in IceBuddha though, I see there is a lot of data after the trailer.
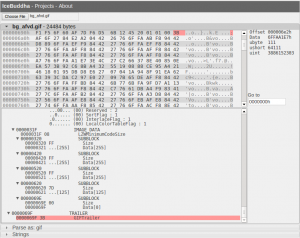
At this point I want to extract out the data after the trailer. I could do this manually, but given that there are a number of MiniDuke gif files, it would be best to do this programmatically. IceBuddha's parse scripts are python code that runs in the browser (using skulpt), but you can just as easily run them locally by cloning the github project https://github.com/0xdabbad00/icebuddha
Once you have that, go to the parse_scripts directory, and from here you can run:
python fileparser.py -t gif ~/Downloads/bg\_afvd.gif</pre>
This will generate the following output:
[
{
"label": "GIF",
"size": 1696,
"data": "",
"offset": 0,
"interpretation": "",
"children": [
{
"label": "GIFHEADER",
"size": 6,
"data": "",
"offset": 0,
"interpretation": "",
"children": [
{
"label": "Signature[3]",
"size": 3,
"data": "",
"offset": 0,
"interpretation": "GIF",
"children": []
},
<snip>
You can get the same data by right-clicking on the parse data in IceBuddha and selecting "Download parsed data".
You could then run this on all the MiniDuke gif files to identify the location of the trailer. I've written a script to find the trailer, extract the key, decrypt the pe file and write it to disk, which you can run as follows:
python example_extractMiniDukeFile.py ~/Downloads/bg_afvd.gif
22790 bytes found at end of file
Extracted file written to: /home/user/Downloads/bg_afvd.gif.infected
This script (part of the github repo) finds the trailer offset:
# Check if GIFTrailer is at the end of the file
parsedData = fileparser.parseFile(filename, filetype)
trailer = fileparser.findElement(parsedData, "GIFTrailer")
trailerOffset = trailer['offset']
It then reads in the file, extracts the key, and decrypts the remainder of the file, which it writes to bg_afvd.gif.infected, This file has the md5sum 297ef5bf99b5e4fd413f3755ba6aad79 which you can search for in virustotal and the search result confirm this is indeed the correctly extracted MiniDuke file.